Cyber Security
Meet Legal Requirements

NIS2 Directive
The NIS2 Directive (Network and Information Security Directive 2) is the EU’s key legislation for strengthening cybersecurity across essential and important sectors. It replaces the original NIS Directive, expanding the scope to include more sectors and introducing stricter security and incident reporting requirements.
High-level requirements include:
Risk-based cybersecurity policies and procedures
Incident detection and reporting within tight timeframes (typically 24 hours)
Supply chain risk management
Accountability at management level
It applies to critical and essential entities in sectors like energy, transport, healthcare, digital infrastructure, and manufacturing.
Cyber Resilience Act (CRA)
The Cyber Resilience Act is a new EU regulation focused on the cybersecurity of digital products and connected devices. Its goal is to ensure that hardware and software products are secure throughout their lifecycle.
Key requirements include:
Mandatory cybersecurity features by design and by default
Ongoing vulnerability management and security updates
Clear documentation for users and regulators
Incident reporting obligations
CRA applies to manufacturers, importers, and distributors of digital products within the EU, making cybersecurity a core product quality requirement.


EU Artificial Intelligence Act (AI Act)
The AI Act is the EU’s first regulatory framework for artificial intelligence, designed to ensure AI systems are safe, transparent, and respect fundamental rights.
Scope and obligations depend on risk levels:
Unacceptable risk: AI systems that are banned (e.g., social scoring)
High-risk: Subject to strict requirements, including data governance, human oversight, and transparency
Limited risk: Transparency obligations (e.g., chatbot disclosures)
Minimal risk: Free to use with no restrictions
The Act applies to developers, deployers, and users of AI systems operating in the EU, even if they are based outside the EU.
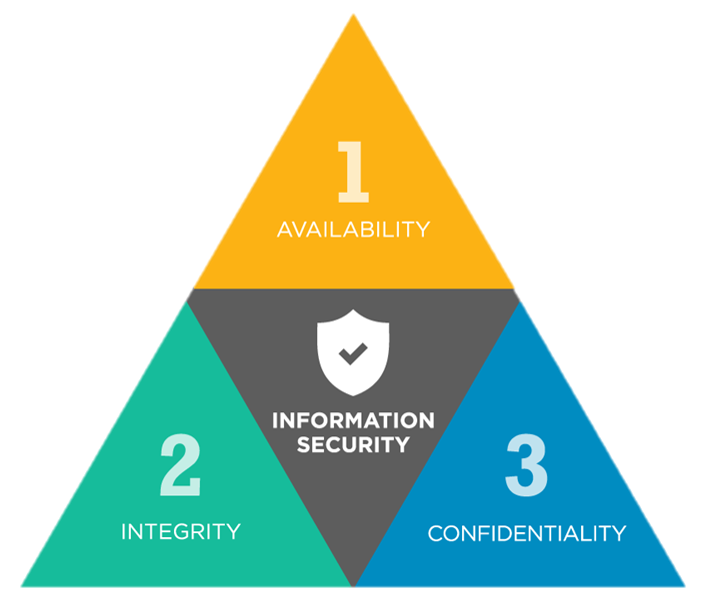
Your Data's DNA: Confidentiality, Integrity, Availability
The CIA Triad is a foundational framework in information security, representing the three core principles of Confidentiality, Integrity, and Availability. It provides a guide for organizations to establish security procedures and policies that address these critical areas.
Here’s a each element:
Confidentiality:
Ensuring that sensitive information is accessible only to authorized individuals or systems, preventing unauthorized access. This includes protecting private data and proprietary information from being viewed, accessed, or used by unauthorized persons.
Integrity:
Guiding against improper information modification or destruction, ensuring that data remains accurate and trustworthy. This includes guaranteeing information non-repudiation and authenticity.
Availability:
Ensuring timely and reliable access to and use of information by authorized users when needed. This means keeping systems, networks, and devices up and running.
The CIA Triad is a widely recognized model that helps organizations plan and implement security controls to mitigate threats and ensure the overall security of their information systems. It’s a key element in developing comprehensive cybersecurity strategies and ensuring the protection of sensitive data